Do you remember what it was like before the internet? If you’re reading this, I bet that there’s a pretty good chance that you don’t, and I may as well be asking, “Do you remember a Land Before Time?” I remeber a time before the internet, I remember when planning a night out with friends…
Identity as opression / Truth as liberation
Since entering the MSW program at the University of Michigan, it has become abundantly apparent that “identity” has taken stage and is the official University of Michigan School of Social Work buzzword. Students are awash with discussions and assertions regarding the need for sensitivity and awareness of intersectionality of identities, identity based oppression, identity…
Ubuntu Dreams of Electric Golden Sheep!
In 2012, Ubuntu, a very popular Linux desktop distribution, decided to strike the beautiful Electric Sheep screen saver program from it’s repositories (think app store), apparently because of some licensing issue or other. This decision also followed a philosophy of “fat trimming”, striking screen savers and other unnecessary bloat from the default set of installed programs, as users no longer needed…
Stolen Generations: Violence of Cultural Conditioning
Reacting to “Rabbit Proof Fence” Rabbit Proof Fence, a 2002 film based on actual events about the Stolen Generations of Aboriginal Australian “half-caste”, or mixed race children, recounts the story of Molly Craig, Daisy Craig Kadibill, and Gracie Fields as they escape a cultural indoctrination camp and make their way back home, on foot, across…
Final Project Proposal
After a careful review of the available options, and spending some time reflecting on class content thus far, I have found myself attracted to the digital story telling option for the final project. I see this as a natural extension of the opening assignment of the course, the Mo’olelo, but with the added opportunity to…
All Pervasive Conditioning: Cultural Assimilation and the Suffocation of Individuality
Culture is the context within which all human interconnectedness occurs, and the intersections of those interconnections is where we find all meaningfulness and all sense of identity. Identity is relational, and relationships necessarily happen within a cultural context; blurred lines delineate the border between the cultural context within which the relationships that shape identity occur,…
Innate Aversion and Blind Oppression: A Buddhist approach to identity based suffering
“An injustice to one is a menace to all,” – Montesquieu This powerful quote captures a certain essence of interdependence, itself sometimes slightly elusive to define. Interdependence, in this sense, is in part an immediate and intimate sense of a common and shared humanity, something directly experienced on a felt level, beyond concept, and almost…
Mo’olelo
“We but mirror the world. All the tendencies present in the outer world are to be found in the world of our body. If we could change ourselves, the tendencies in the world would also change. As a man changes his own nature, so does the attitude of the world change towards him. This…
Protecting Dissent: How to set up a Tor Hidden Service in Ubuntu 16.04
“When you do something you should burn yourself completely, like a good bonfire, leaving no trace of yourself.” ~Shunryu Suzuki In America, Freedom of Speech is a protected constitutional right. It protects our ability to openly dissent and criticize the government and sitting administration without fear of being silenced or threatened by the strongest authority in…
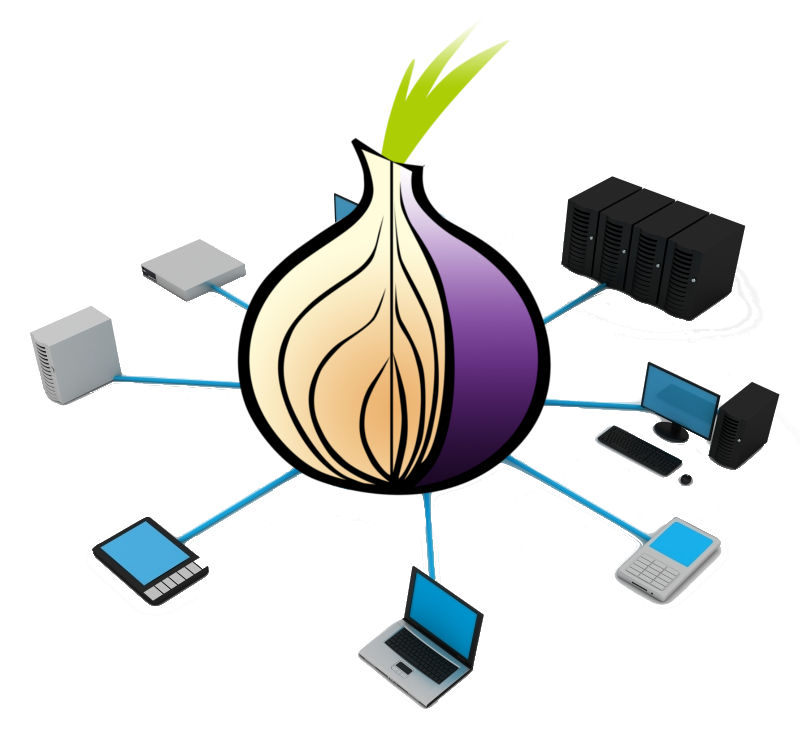
Giving back to Tor: How to run a relay server
E Pluribus Unum Magnum Cepa Tor, or The Onion Router, is the software equivalent of an iron clad shield to the 1st amendment to the Constitution of the United States of America. It protects user anonymity and privacy, allows a user to access hidden, deeply secure, and secretive parts of the internet, and allows website owners to operate…